Business Intelligence Tools to Automatically Mask PII: A Comprehensive Guide
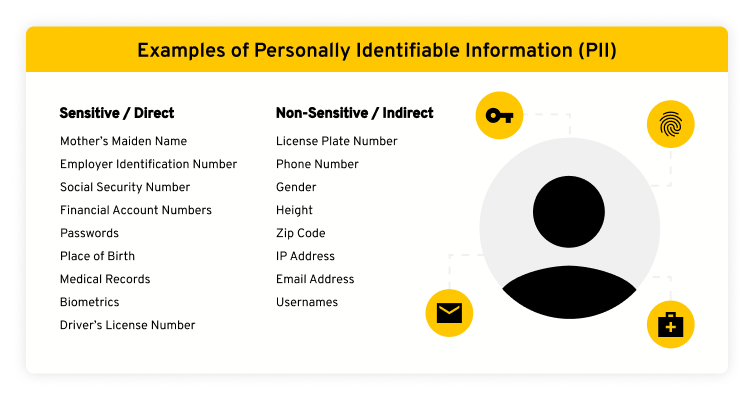
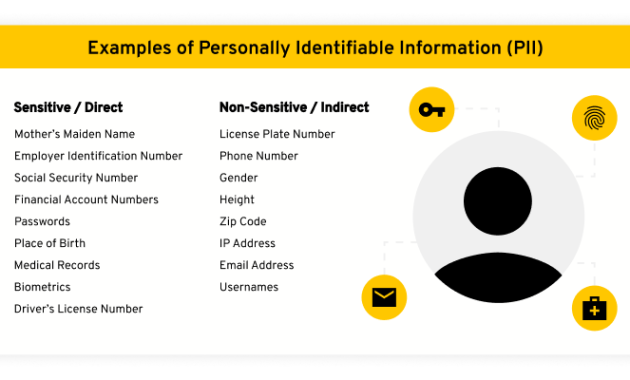
In today’s data-driven world, businesses rely heavily on data analytics and business intelligence (BI) to make informed decisions. However, this reliance brings with it significant challenges, particularly concerning the protection of Personally Identifiable Information (PII). PII, which includes data like names, addresses, social security numbers, and medical records, is highly sensitive and subject to stringent regulations like GDPR and CCPA. The use of Business Intelligence tools to automatically mask PII has become increasingly critical for organizations seeking to comply with these regulations, safeguard customer privacy, and mitigate the risks associated with data breaches.
This guide delves into the critical role of business intelligence tools to automatically mask PII, exploring their functionalities, benefits, and implementation strategies. We will examine the key features of these tools, their impact on data privacy and security, and how businesses can effectively leverage them to navigate the complex landscape of data protection.
Understanding the Importance of PII Masking
Before diving into the tools, it’s essential to understand why PII masking is so crucial. Data breaches can lead to significant financial losses, reputational damage, and legal penalties. Furthermore, non-compliance with data privacy regulations can result in hefty fines and legal action. PII masking is a proactive approach to protecting sensitive data by concealing or redacting it, rendering it unidentifiable to unauthorized users while still allowing for data analysis.
Masking is not the same as encryption. Encryption transforms data into an unreadable format, requiring a key for decryption. Masking, on the other hand, alters the data in a way that it is no longer directly identifiable but retains its utility for analysis. For example, a masking tool might replace a customer’s actual name with a pseudonym or replace a portion of a social security number with asterisks.
Key Features of Business Intelligence Tools for PII Masking
Effective business intelligence tools to automatically mask PII typically offer a range of features designed to simplify and automate the data protection process. These features include:
- Data Discovery and Classification: The ability to identify and classify PII within datasets automatically. This feature uses algorithms to scan data sources and flag sensitive information.
- Masking Techniques: A variety of masking methods, such as pseudonymization, redaction, anonymization, and data obfuscation, to protect PII.
- Automated Workflows: Pre-configured workflows and automation capabilities to streamline the masking process, reducing the need for manual intervention.
- Role-Based Access Control: Granular control over who can access masked and unmasked data, ensuring that only authorized personnel have access to sensitive information.
- Audit Trails and Reporting: Comprehensive audit logs to track data masking activities and generate reports for compliance purposes.
- Integration Capabilities: Seamless integration with various data sources, BI platforms, and data warehouses to ensure a cohesive data protection strategy.
Benefits of Using BI Tools for PII Masking
Implementing business intelligence tools to automatically mask PII provides several significant advantages for organizations:
- Enhanced Data Privacy: Protecting sensitive customer data from unauthorized access and misuse.
- Compliance with Regulations: Ensuring compliance with data privacy regulations like GDPR, CCPA, and HIPAA.
- Reduced Risk of Data Breaches: Minimizing the risk of data breaches and the associated financial and reputational damage.
- Improved Data Security: Strengthening data security posture and protecting against insider threats.
- Streamlined Data Analysis: Enabling data analysts to work with masked data while still performing meaningful analysis.
- Cost Savings: Reducing the costs associated with manual data masking and compliance efforts.
Implementing Business Intelligence Tools for PII Masking: A Step-by-Step Guide
Implementing business intelligence tools to automatically mask PII requires a systematic approach. Here’s a step-by-step guide:
- Assess Data Inventory: Identify all data sources and data types, including PII.
- Choose the Right Tool: Select a BI tool that offers robust PII masking capabilities and aligns with your organization’s needs. [See also: How to Choose the Right BI Tool]
- Define Masking Rules: Establish clear rules for masking PII based on data types and regulatory requirements.
- Configure the Tool: Configure the tool to automatically mask PII according to the established rules.
- Test and Validate: Test the masking process to ensure that PII is effectively masked and that data analysis can still be performed.
- Implement Role-Based Access Control: Grant access to masked and unmasked data based on user roles and permissions.
- Monitor and Maintain: Continuously monitor the masking process and update rules as needed to ensure ongoing compliance.
Popular Business Intelligence Tools with PII Masking Capabilities
Several business intelligence tools to automatically mask PII are available on the market. Some of the leading options include:
- Tableau: A popular BI platform that offers data masking capabilities through calculated fields and row-level security.
- Power BI: Microsoft’s BI platform provides data masking features through security roles and dynamic data masking.
- Looker: A modern BI platform that offers robust data governance and PII masking capabilities through its data modeling layer.
- ThoughtSpot: A search-driven analytics platform with built-in data masking features and role-based access control.
- Qlik Sense: A data visualization and analytics platform that provides data masking through section access and other security features.
It’s crucial to evaluate the specific features and capabilities of each tool to determine the best fit for your organization’s needs.
Best Practices for PII Masking with BI Tools
To maximize the effectiveness of business intelligence tools to automatically mask PII, consider these best practices:
- Start with a Data Privacy Assessment: Conduct a thorough assessment to identify all PII and the risks associated with its use.
- Develop a Data Masking Policy: Create a comprehensive data masking policy that outlines the rules and procedures for masking PII.
- Train Your Team: Provide training to data analysts and other users on the importance of data privacy and the proper use of masked data.
- Regularly Review and Update Masking Rules: Review and update masking rules periodically to reflect changes in regulations and data sources.
- Monitor and Audit Data Masking Activities: Implement robust monitoring and auditing mechanisms to track data masking activities and ensure compliance.
- Prioritize Data Minimization: Only collect and store the minimum amount of PII necessary to meet your business needs.
- Consider Data Anonymization: Where possible, consider anonymizing data rather than simply masking it, to remove the ability to re-identify individuals.
Future Trends in PII Masking and Business Intelligence
The landscape of data privacy and BI is constantly evolving. Several trends are shaping the future of business intelligence tools to automatically mask PII:
- Increased Automation: Further automation of the data masking process, including automated data discovery, classification, and masking.
- AI-Powered Masking: The use of artificial intelligence (AI) to improve the accuracy and efficiency of data masking.
- Enhanced Data Governance: Tighter integration of data masking with broader data governance frameworks.
- Focus on Privacy-Enhancing Technologies (PETs): Adoption of PETs, such as homomorphic encryption and differential privacy, to protect sensitive data.
- Cloud-Based Solutions: The increasing adoption of cloud-based BI tools with built-in PII masking capabilities.
These trends highlight the growing importance of data privacy and the need for organizations to invest in robust PII masking solutions.
Conclusion: Securing Data and Building Trust
In conclusion, business intelligence tools to automatically mask PII are essential for businesses navigating the complexities of data privacy and security. By implementing these tools and following best practices, organizations can protect sensitive data, comply with regulations, and build trust with their customers. As data volumes continue to grow and data privacy regulations become stricter, the importance of PII masking will only continue to increase. Investing in the right tools and strategies is a critical step towards ensuring a secure and compliant data environment.
The proper implementation of these tools will help businesses leverage the power of data while maintaining the highest standards of privacy and security. Businesses must prioritize data privacy and security, and business intelligence tools to automatically mask PII represent a vital component of that effort.
By understanding the capabilities and the best practices for employing these tools, organizations can confidently navigate the data landscape and build a sustainable and compliant data strategy.
The ability of business intelligence tools to automatically mask PII to adapt to evolving data privacy regulations and security threats is a testament to the commitment of the technology to protecting sensitive information.
The right implementation of business intelligence tools to automatically mask PII can ensure that businesses can harness the power of data analysis while maintaining the highest standards of privacy and security.
Ultimately, the effective use of business intelligence tools to automatically mask PII is not just about compliance; it is about building a culture of trust and respect for data privacy.
Choosing the right business intelligence tools to automatically mask PII and implementing them effectively is crucial for any organization that handles sensitive data.
Proper use of business intelligence tools to automatically mask PII enables businesses to make informed decisions while upholding data privacy.
Finally, remember that the success of business intelligence tools to automatically mask PII depends on a combination of the right technology and the right policies.